The reason for gaining access to someone else’s social media data can vary, but the methods for doing so are few.
If you have already searched the internet for other solutions, you must be saying “Few? I found several! ”. Well, actually, there are many.
However, the overwhelming majority of them fall into two classes: outdated methods that have already been overcome by digital security technologies and those that are actually frauds, aimed at harming those who believe.
In a search on Google, we can see thousands of “tools” or “technical” to hack the Instagram of another person by cell phone, the computer, as well as sites to hack Instagram. Many say they are free.
Instagram is one of the largest social networks today, with over 100 million users, with great traffic information. Is it so easy to offer methods to hack this platform? Does this method not even have a cost for its developer, to the point that it is worth offering it to the public free of charge?
WHAT IS INSTAGRAM?
Instagram, as we said, is one of the largest social networks in 2020. In this platform, millions of people connect, post photos, and videos, exchange messages.
The platform, owned by Facebook CEO Mark Zuckerberg, also moves millionaire figures, through various forms of advertising, used by artists, celebrities, large and small companies and even ordinary people.
This also brings to light the major investments made by Instagram and other major social networks in defending their domains and protecting data, whether their own, or those who use their varied services.
Instagram can be accessed by a browser, on your website, or in application versions for iOS and Android.
WHAT IS HACKING?
Hacking is the action of obtaining knowledge in the digital world. The information that you should not have. Generally, hackers are individuals who have great knowledge of programming and coding and are able to invade Instagram, Facebook, banks, and public agencies, among others.
So basically, hacking Instagram is getting access to someone else’s private information. In-depth knowledge of programming and coding is generally characteristic of hackers.
IS IT POSSIBLE TO HACK ANOTHER PERSON’S INSTAGRAM? IT’S FREE?
The answer is yes, it is possible. However, unless you’re a person with deep knowledge, like hackers, hacking into someone else’s Instagram can cause the target user to know.
It turns out that when we do a quick search on any search engine – like Google. We find numerous sites, Apps and tutorials that promise access to any information, above all, free of charge!

Now let’s stop and think about it. Companies the size of Instagram, large banks, and government agencies in countless countries invest millions of dollars to ensure the safety of their services and products.
The Instagram company develops products or services, keeps applications or software updated, and provides help. Can you really find free hacking methods on the Internet to achieve what you want?
If you answered no, you were right. Obviously, most Apps, websites, and other fantastic solutions are viruses.
They steal user data, and make unpopular advertisements and other promises to promote the software.
However, as we will show below, there are some Apps that perform the task with safety, support, and quality. Of course, they are not free, as they require a lot of effort and technology to make this mission possible. Don’t worry, we chose a complete App with a price that fits in your pocket!
WHAT ARE THE BEST APPS FOR HACKING INSTAGRAM?
We analyzed several services, paid and free, in order to guarantee the best choice for you!
We take into account the variety of services offered, the price, the credibility and the certainty of fulfilling the objective, customer service, and of course, security.
The mSpy, for the uninitiated, is the most full-service digital monitoring there. With a very simple interface, an affordable price, and a complete range of functions. You can follow the step of your child, wife, husband, or anyone else, on the internet and on your smartphone.
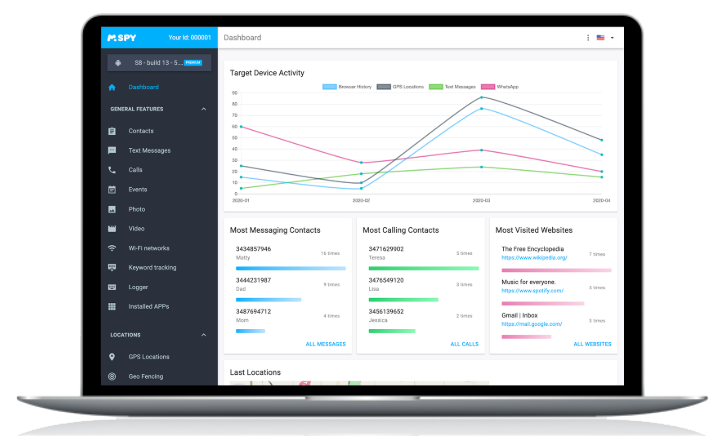
The mSpy offers an application called “spy on Instagram”, which allows users to connect all sent and received information to shared personal data, and allows monitoring people to access these data.
Through a simple and intuitive control panel, you will be able to follow the movements of the monitored person at all times.
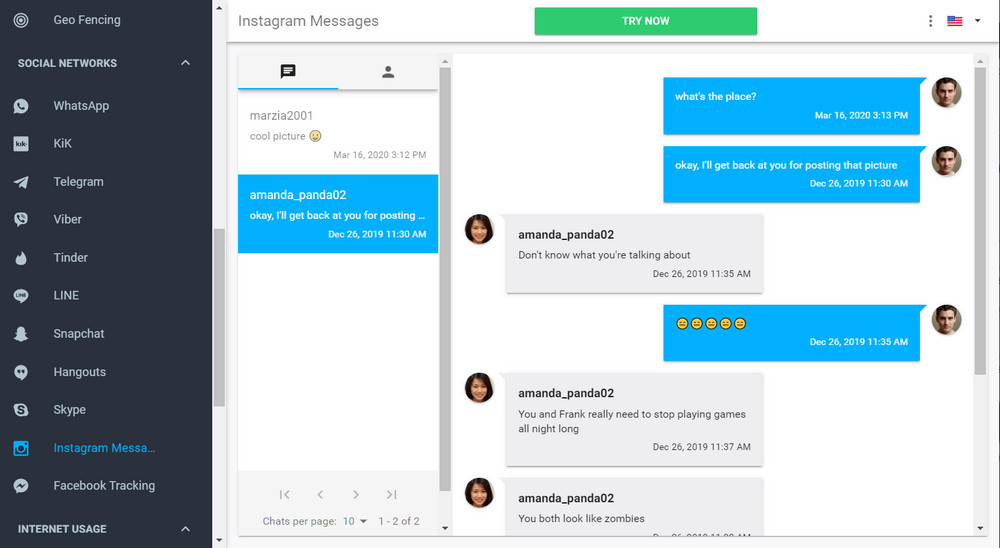
The mSpy is compatible with Android and iOS. With state-of-the-art technology, the App runs invisibly to the monitored person and has not shown significant battery consumption or loss of smartphone processing capacity.
The mSpy triggered our recommendation for an efficient monitoring, safe and without the need for any knowledge of programming or coding.
With mSpy’s Instagram Tracker, you know everything that goes on the other person’s Instagram.
HOW CAN I PROTECT MY INSTAGRAM ACCOUNT?
What if someone wants to monitor our account? How to protect account security?
Like almost everything in life, there are ways to prevent or at least hinder access to your personal data and accounts, on Instagram and other platforms in general.
Below, we’ve listed some simple yet effective ways to make your Instagram account more secure:
NEW ACCOUNT RECOVERY MODE ON INSTAGRAM
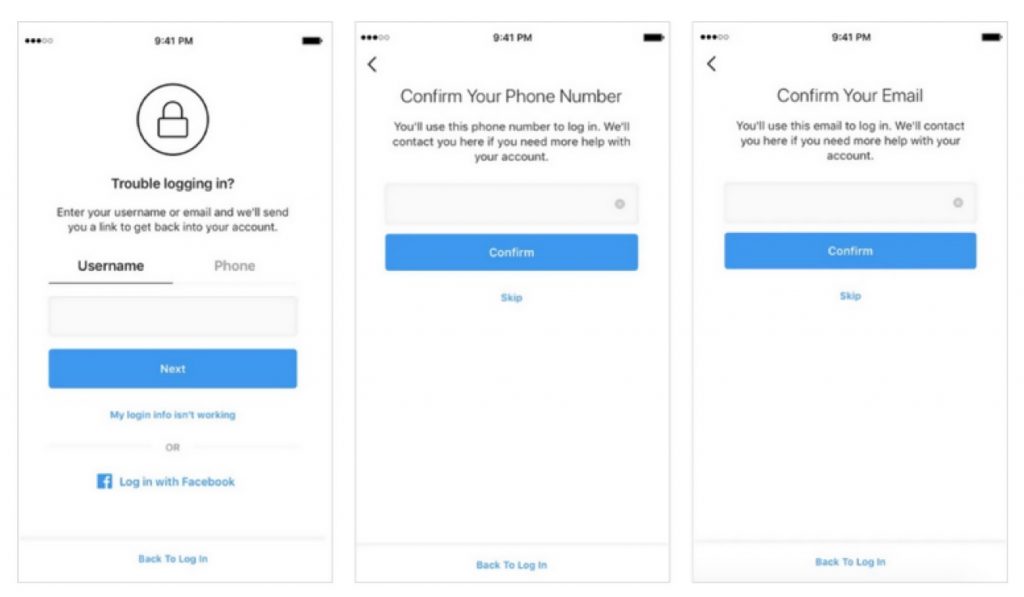
Some time ago, Instagram announced an innovative process to recover your account, after it was hacked. If you no longer have access to your previous account, for example, a change in your password made by an unauthorized third party. This method should give all your “migrated” content to a new secure account, to which only you access. Invalidating the previous one, to which the attacker had access.
CHOOSE A SECURE PASSWORD
There is a lot of online material available to assist you with a secure choice for your Instagram password. The platform itself provides assistance in choosing. In general, avoid using dates, names, nicknames and other words, in some way, refer to your life. Remember that our life, nowadays, is wide open on the internet for those who want to see it.
This information may seem obvious, but look at your passwords: none of them contain your initials? Your dog’s name or year of birth? Who knows the whole date of your birthday?
USE A COMPLETE ANTI-VIRUS
You may find it silly or an unnecessary expense. But, if your account is invaded, the headache and damage will be hundreds of times the amount invested in an antivirus.
There are several products and services with great prices, and complete services, which prevent attackers from accessing your computer and your social networks. We are never sure that the link we want to click on is completely secure.
This is an additional security measure that is simple to incorporate, with low cost but often ignored by ordinary users.
PROTECT YOUR EMAIL
Imagine that your Instagram account is your home or apartment. The corridor or garden you pass every day until you actually enter your home is your email. That’s right, this is not the main way to invade your account, but it is also one.
Using an antivirus is also useful here. But, you can also take simple precautions, such as not writing your email on any website, and not subscribing to any list of content with your email.
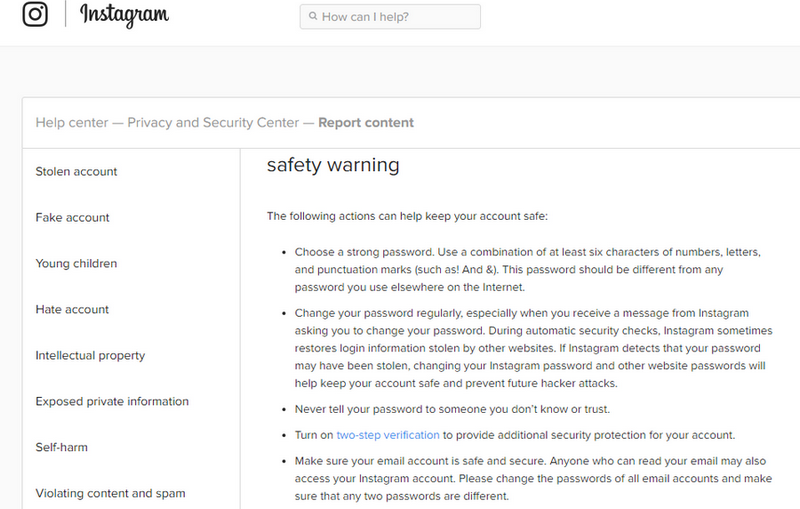
USE THE TIP OF SAFETY ON INSTAGRAM
This is a basic principle. Companies like Instagram invest millions of dollars in security. It is natural for them to know the best protection practices. Part of these practices, of course, is their responsibility. Another is under the responsibility of users. Read the security section carefully and see simple ways on how you can increase the security of your account.
OUR CONCLUSION
After reviewing several spy apps, reviewing features, prices, compatibility, and especially, security, there is no other to recommend. As we said, our recommendation is mSpy.
Here you learned, that it is impossible to offer an App or software capable of monitoring a person’s Instagram at zero cost. So, why do we find options when we look?
Simple! Your data is worth money. Be it later extortion against you, or the sale of your data to companies interested in knowing more about you, they are worth money.
Worse, this can trigger a series of problems of the most varied severities, if your data falls into the wrong or malicious hands. Imagine having your credit card number, password, and verification code stolen, or appropriated by someone else?
And, what better way to get them than to access everything you have registered on the internet and on your smartphone?
It is important to highlight that the use of monitoring tools is the responsibility of each user. Be aware of your choice and use. Do not run any more problems with mistakes that can be expensive.


